Keep In Mind, log administration is an ongoing course of, and it’s normal to come across issues alongside the greatest way. For instance, your builders may want entry to error logs for troubleshooting, however they probably don’t want access to security logs. By limiting entry, you’ll have the ability to reduce the danger of logs being tampered with or uncovered. Plus, it integrates properly with different instruments, like Kibana for creating dashboards and Logstash for log processing.
Log Evaluation: Making Sense Of Your Information
In these instances, you have to work out tough guides to server capability requirements, primarily based on the system requirements listed for the software program that you buy to turn on the server. Over time, you will be able to collect utilization statistics through monitoring and consolidate these figures in an analytical software. New necessities positioned on the server will have to be added to the current capability to estimate whether you have enough sources to cope. There are several elements that the system administrator should look out for to ensure that the server is constantly obtainable and performing well.
Structured Format
This predictive stance fortifies networks towards rising assault vectors and uncovers root causes sooner. Automated retention, compliance monitoring, and AI-driven anomaly detection increase resilience. Over time, continuous log analytics fosters a culture of data-driven improvements—enhancing efficiency, minimizing breach influence, and ensuring long-term operational stability.
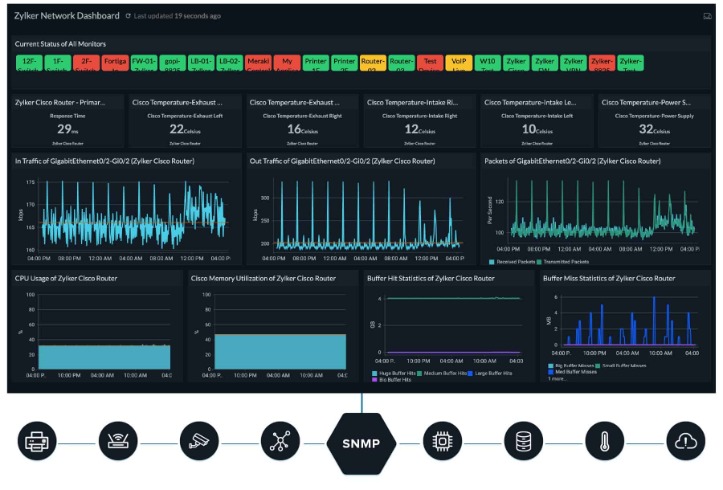
- The key attributes to observe are CPU usage, memory consumption, I/O, community capacity and activity levels, and disk utilization.
- This follow helps in figuring out potential safety threats effectively.
- Constructing dashboards and establishing alerting helps you monitor your logs in real-time.
- Implementing real-time monitoring and alerts ensures you could respond to points as they arise.
- To successfully safe your log knowledge, implement encryption and ensure information in transit is protected with SSL/TLS protocols.
This is why it is essential to have the power to correlate log files with one another and with different sources of visibility – such as, again, metrics and traces. In addition to generating stories, logs also can trigger alerts about potential points that the IT group should examine instantly. Alerts do not Servers Expert summarize overarching tendencies, but they do help guide an efficient response to efficiency points. Copying logs to central storage ensures that the log information will persist even if the unique logs disappear. Traces can provide even deeper insights into particular transactions or request paths, especially in cloud-native environments.